3-D Secure Payment or 3DS - (3-Domain Secure Payment)
By: Baski in Java Tutorials on 2007-09-14
Payment Authentications are designed to stop credit card fraud by authenticating cardholders when performing transactions over the Internet by using the 3-Domain Secure (3-D Secure or 3DS) protocol developed by Visa.
A 3-D Secure transaction is performed immediately before a merchant performs a payment transaction, that is, Authorisation transaction in the Auth/Capture mode; and the Purchase transaction in the Purchase mode. Authentication ensures that the card is being used by its legitimate owner. During a transaction, it allows the merchant to authenticate the cardholder by redirecting them to their card issuer where they enter a previously registered password.
Note: 3-D Secure Authentication can only take place if the merchant is using a Payment Authentication model as the cardholder's browser has to be redirected to their card issuing bank where they enter their secret password.This is performed by the Payment Server if the cardholder is enrolled in the 3-D Secure schemes of Verified by Visa and MasterCard SecureCode
Payment Authentication 3-D Secure transaction modes
The available Payment Authentication 3-D Secure transaction modes for Verified by Visa and MasterCard SecureCode are:
Mode 3a - Payment Authentication - Authentication Only transaction - the merchant uses the Payment Server to perform an authentication transaction and the payment transaction is processed as a separate transaction. This gives the merchant complete control as to when and if a payment transaction should proceed. The Authentication operation outputs become the inputs for a Payment Authentication with card details transaction. The merchant needs to collect card details.
Mode 3b - Direct Payments Style Pre-Authenticated Payment transaction - the merchant may use the Payment Authentication - Authentication only transaction through the Payment Server or an external authentication provider to perform the 3-D Secure Authentication, and use the outputs from this operation to perform a Direct Payments transaction through the Payment Server. The merchant needs to collect card details.
Information Flow of a 3D-Secure Authentication/Payment transaction
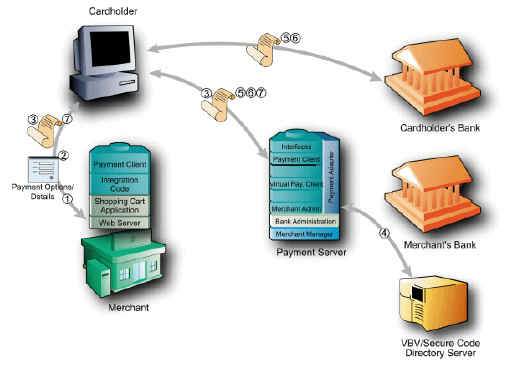
If you have been enabled to use Verified by Visa and MasterCard SecureCode, the information flow for Verified by Visa and MasterCard SecureCode where the merchant collects the card details for use in an Authentication Only (Mode 3A) is as follows:
- A cardholder browses the application, selects a product and enters their shipping details into the merchant's application at the checkout page.
- The cardholder clicks a pay button and the merchant application prompts the cardholder for their card details.
- Once these are captured the merchant application redirects the cardholder's Internet browser to the Payment Server, which takes the encrypted Digital Order to the Payment Server .
- If the card is a Visa or MasterCard, the Payment Server then checks with the VBV or SecureCode Directory Server to determine if the card is enrolled in either the Verified by Visa or MasterCard SecureCode scheme.
If the cardholder's card is registered in the payment authentication scheme, the Payment Server redirects the cardholder's browser to the card issuing bank site for authentication. If the cardholder's card is not registered in the payment authentication scheme, the Payment Server redirects the cardholder's browser back to the merchant's site indicating the card is not registered - see step 7. - If the cardholder's card is registered in the payment authentication scheme, the Payment Server redirects the cardholder's browser to the card issuer's site for authentication. The card issuer's server displays the cardholder's secret message and the cardholder enters their response (password), which is checked against the Issuing bank's database.
- At the completion of the authentication stage, the cardholder is redirected back to the Payment Server indicating whether or not the cardholder's password matched the password in the issuing bank's database.
- The Payment Server then redirects the cardholder back to merchant's site with the Digital Receipt. The Digital Receipt contains the result of the Authentication operation, where the merchant application decrypts the Digital Receipt ready for the Direct Payments payment,
Note: If the cardholder is enrolled in the 3D Secure scheme but is not authenticated correctly, for example, because the cardholder may have entered their password incorrectly 3 times, then the merchant's application is sent a response code of 'F' to indicate the cardholder failed the authentication process.
Add Comment
This policy contains information about your privacy. By posting, you are declaring that you understand this policy:
- Your name, rating, website address, town, country, state and comment will be publicly displayed if entered.
- Aside from the data entered into these form fields, other stored data about your comment will include:
- Your IP address (not displayed)
- The time/date of your submission (displayed)
- Your email address will not be shared. It is collected for only two reasons:
- Administrative purposes, should a need to contact you arise.
- To inform you of new comments, should you subscribe to receive notifications.
- A cookie may be set on your computer. This is used to remember your inputs. It will expire by itself.
This policy is subject to change at any time and without notice.
These terms and conditions contain rules about posting comments. By submitting a comment, you are declaring that you agree with these rules:
- Although the administrator will attempt to moderate comments, it is impossible for every comment to have been moderated at any given time.
- You acknowledge that all comments express the views and opinions of the original author and not those of the administrator.
- You agree not to post any material which is knowingly false, obscene, hateful, threatening, harassing or invasive of a person's privacy.
- The administrator has the right to edit, move or remove any comment for any reason and without notice.
Failure to comply with these rules may result in being banned from submitting further comments.
These terms and conditions are subject to change at any time and without notice.
- Data Science
- Android
- React Native
- AJAX
- ASP.net
- C
- C++
- C#
- Cocoa
- Cloud Computing
- HTML5
- Java
- Javascript
- JSF
- JSP
- J2ME
- Java Beans
- EJB
- JDBC
- Linux
- Mac OS X
- iPhone
- MySQL
- Office 365
- Perl
- PHP
- Python
- Ruby
- VB.net
- Hibernate
- Struts
- SAP
- Trends
- Tech Reviews
- WebServices
- XML
- Certification
- Interview
categories
Related Tutorials
Read a file having a list of telnet commands and execute them one by one using Java
Open a .docx file and show content in a TextArea using Java
Step by Step guide to setup freetts for Java
Of Object, equals (), == and hashCode ()
Using the AWS SDK for Java in Eclipse
DateFormat sample program in Java
concurrent.Flow instead of Observable class in Java
Calculator application in Java
Sending Email from Java application (using gmail)
Comments